The update we provided on February 13th with Bricks 1.9.6.1 was a quick and effective answer to the vulnerability reported on February 10th. It successfully tackled the urgent issue and also initiated a broader initiative to strengthen Bricks’ security rather than representing the final phase of our security enhancements.
We’ve dedicated the past four weeks to a thorough review and enhancement of our entire codebase. Our goal was clear: develop a solution for code execution that maintains the advanced code functionality you rely on while elevating Bricks’ default security level to new heights.
This 1.9.7 update is the result of this effort. It introduces a suite of new security features and improvements.
It also addresses a smaller, possible authenticated issue discovered while working on 1.9.7, which requires a contributor role or above, bad intentions, and a code execute user to perform certain additional steps. There is no need to panic or update in the next 5 minutes, but we recommend updating as soon as you have the chance.
If you experience any problems after updating, please reach out to us via email at [email protected].
Before you update, please take a full backup of your site!
The significant changes of this update could impact your site’s functionality. A backup ensures you have a safe point to revert to if necessary. Please do not skip this critical step.
Breaking changes for enhanced code security
In this update, we have made some changes that will affect existing features – what we commonly refer to as “breaking changes.” We want to acknowledge that such updates can be disruptive and are not decisions we make lightly. However, in this case, they are necessary to ensure the highest security and functionality standards for Bricks over the years to come.
Bricks 1.9.7 introduces the following new security features and significantly updates and strengthens existing ones, ensuring a more secure and advanced experience for all users.
- Code execution: Code execution is now disabled by default, which is how it should have been from the beginning. It is an opt-in feature for advanced users who want to utilize it.
- Code signature: If you choose to enable code execution, there’s an added layer of security. Any code that runs must be signed by a user with full builder access and code execution capability. This means only trusted code will execute.
- Code review: We introduce this new feature to let you review all executable code on your site added through Bricks. It’s an extra step to ensure your site runs safely and sound.
- Echo tag function filter: All functions called through the dynamic “echo” tag must be explicitly whitelisted via a new Bricks filter.
Code execution: Disabled by default
If you don’t use any of the following four features on your Bricks site, you don’t need to perform any additional steps after updating to Bricks 1.9.7. We still recommend that you continue reading to learn what has changed if you want to use those features in the future.
After updating to Bricks 1.9.7 and above, code execution is disabled by default. This means the following elements/instances no longer run by default:
- All Code elements with “Execute code” enabled
- All SVG elements with “Source” set to “Code”
- All Query editor instances
- All dynamic “echo” tags
Reflecting on our continuous improvement ethos, this default treatment of code execution aligns more closely with our commitment to security best practices.
How to enable code execution
To enable code execution, go to Bricks > Settings > Custom code and check the Enable code execution setting.
Then, enable code execution for the user roles below the setting or individual users by editing their user profiles directly.
Code signatures
This unique new security feature ensures the integrity of the code executed. Signatures act as a safeguard, verifying that any code running on your site has not been altered or tampered with.
This process involves creating a unique digital signature for each piece of code, which is validated whenever the code is executed.
If a code’s signature does not match its stored validation, indicating potential unauthorized modifications, it won’t run.
Only users with full builder access & code execution can create these signatures, either individually within the builder, in bulk, or globally under Bricks settings.
You can sign code individually when editing the code in the builder, in bulk using the unsigned code manager in the builder, or globally under “Custom signatures” at Bricks > Settings > Custom code.
Documentation: https://academy.bricksbuilder.io/article/code-signatures/.
Before you sign your code globally via the Bricks settings, make sure to review any code using the new “Code review” feature in Bricks 1.9.7.
Troubleshooting code signatures: There’s a new bricks/code/disable_signatures that allows you to disable code signatures programmatically. It’s only meant as a temporary solution that we intend to remove as soon as we know code signatures are working flawlessly. Use this filter only if all users on your site are trustworthy. For more information, https://academy.bricksbuilder.io/article/filter-bricks-code-disable_signatures/.
Code review
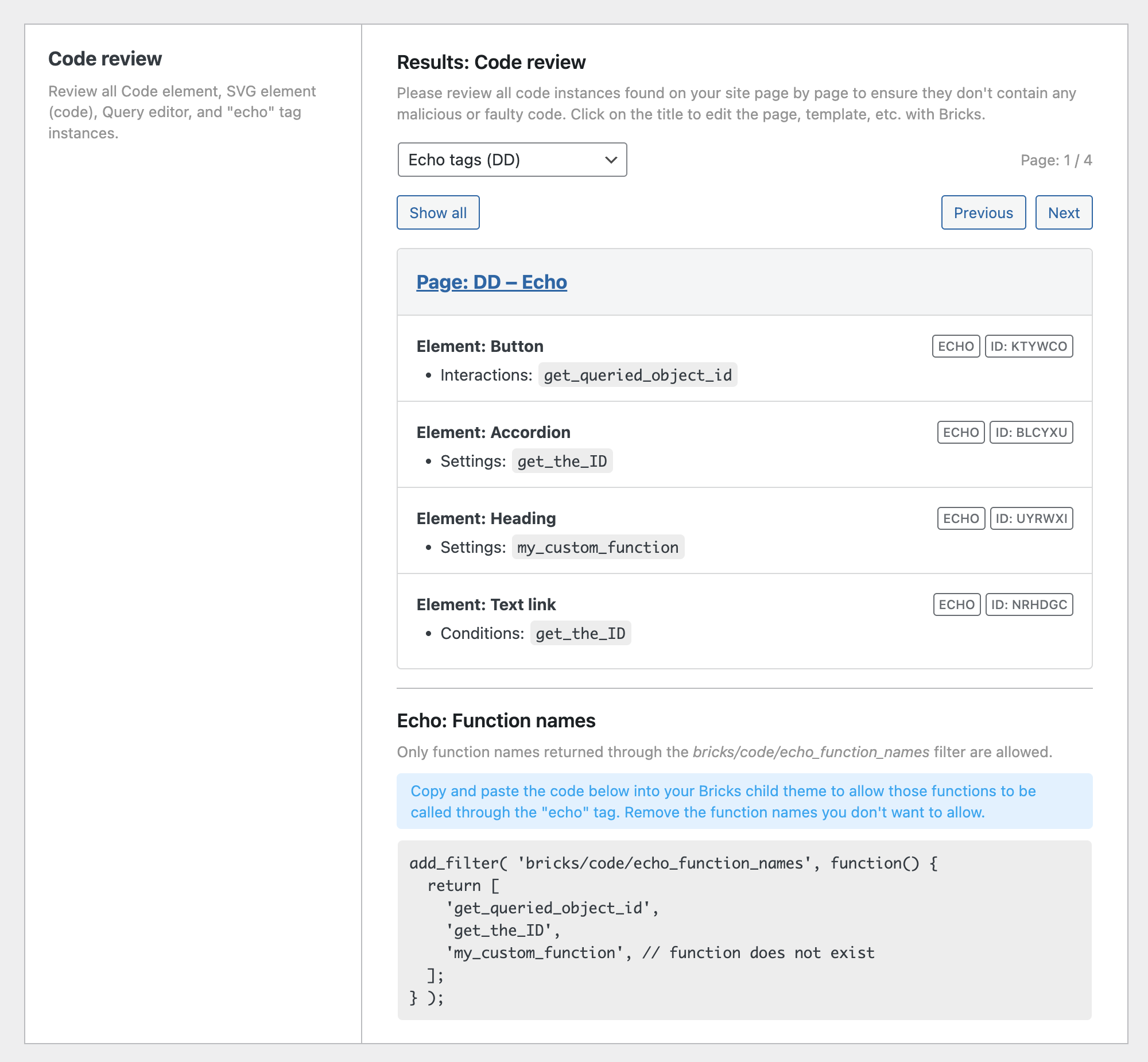
The Code review is a proactive security tool that allows you to view all executable code instances and dynamic “echo” tags on your Bricks site on one screen.
To start a Code review, go to Bricks > Settings > Custom code > Code review and click the “Start: Code review” button.
You can go over the results of your code review page-by-page or all-at-once and see which code has a valid signature or might contain invalid or potentially dangerous code.
Once you have confirmed the integrity of the code on your website, you can globally sign all code instances on your site by clicking the “Regenerate code signatures” button further down the same Bricks settings tab.
Documentation: https://academy.bricksbuilder.io/article/code-review/
Enable “echo” tag functions through Bricks filter
The dynamic “echo” tag is another powerful and advanced Bricks feature.
Instead of verifying it through code signatures, you have to allow/whitelist individual function names via the new bricks/code/echo_function_names filter.
Documentation: https://academy.bricksbuilder.io/article/filter-bricks-code-echo_function_names/
Manually inspecting your entire site for all “echo” tag occurrences is often impossible. Instead, you can run a Code review.
At the bottom of the code review results, you’ll see a code snippet that contains all function names called through an “echo” tag on your site.

You can copy the generated code snippet and paste it into the functions.php file of your Bricks child theme or the code snippet plugin of your choice.
Make sure to remove any function names that might be called, but you don’t want to allow. Function names that don’t exist are marked so by the // function does not exist comment after the function name.
Update checklist for Bricks 1.9.7
- Perform a full-site back.
- Update to Bricks 1.9.7.
- Initiate code review: Go to
Bricks settings > Custom code > Code review. Click “Start: Code review” to retrieve all executable code instances on your site. - Enable code execution (if needed): If you use features like Code elements with “execute code” enabled, SVG elements with “source” set to “code”, query editor instances, or dynamic “echo” tags, enable this option in
Bricks > Settings > Custom code. - Generate code signatures (mandatory if code execution is enabled): If you have enabled code execution, you must generate code signatures for all executable code. Click on “Regenerate code signatures” in
Bricks > Settings > Custom code > Code signaturesto automatically generate these signatures site-wide. - Add echo tag functions to new filter (if used): Initiate a code review (see step 3) to automatically generate a filter of function names used in dynamic “echo” tags. Copy this auto-generated filter and paste it into the
functions.phpfile of your Bricks child theme. Make sure to remove any unwanted function names. This step is necessary to allow specific functions to be used with “echo” tags.
As we close this update announcement, we want to emphasize the commitment and effort that has gone into making Bricks 1.9.7 a substantial step forward in our journey. We’ve worked tirelessly to not only address immediate security concerns but also to lay a stronger foundation for the future of Bricks.
We thank you for your continued support and understanding as we navigate these improvements together. Your feedback and engagement are invaluable to us. If you have any questions or need assistance, we’re here to help.
Full changelog
- Code execution: Disabled by defaultNew
- Code signaturesNew
- Code reviewNew
- Filter: Radio & Checkbox indentation prefix & gap settingNew
- Filter: Checkbox, Radio & Select: New setting “Label: All terms”New
- Post comments: New “Fields” setting & Support WP filter comment_form_default_fieldsNew
- Always show “Enable auto-updates” link for Bricks (Appearance > Themes)New
- Disable Autoptimize plugin in builderImprove
- Remove empty array in global classes before save to databaseImprove
- splide.min.js not minifiedImprove
- Image Gallery: Use real images (instead of background images)Improve
- Bricks settings: Rename and move “Add element ID as needed” setting from “Performance” to “General” tabImprove
- Posts element: Use real images (instead of background images)Improve
- Related Posts element: Use real images (instead of background images)Improve
- Builder: Background control (popup) color tooltip not showingFix
- Code element: Not rendered on frontend if global element or inside templateFix
- Color palette: Color changes when changing transparencyFix
- Form: Save submission with non-latin characters (page slug)Fix
- Query loop: HTML comment as query result placeholder not working looping tr tagFix
- Query loop: PHP error with term includesFix
- Query filter: Index table missing (creation error MariaDB)Fix
- WooCommere: Notices not styleable in WooCommerce 8.6Fix
- WooCommerce: Sale badge percentage error if set by plugin or hookFix
- Builder: 1st loop item value not rendered correctlyFix
- Code element: All backslashes removed if saved by Edit Content userFix
- Image element: border-radius not applied (link, figure)Fix
- Builder: Allow ‘Edit content’ user to sort/DnD element items (Accordion, Slider, Image gallery, Carousel, etc.)Fix
- Query loop: No results text causing overflowFix
- Lightbox script (Photoswipe) enqueued with just lightboxId setFix
- Icon font enqueue not workingFix
- Bricks settings: Custom auth dropdowns not showing all pages with WPML/PolylangFix